GoDaddy Discloses Multi-Year Security Breach That Resulted In Malware Installs, Source Code Theft
(The AEGIS Alliance) – GoDaddy, which provides web hosting services, has recently announced a security breach that took place over several years, resulting in malware installation and the theft of source code related to some of its services by unknown actors. The company believes the attack was carried out by a highly sophisticated and organized group that specifically targeted hosting services.
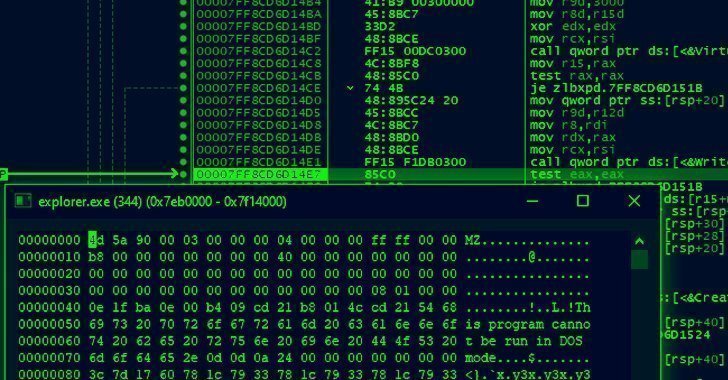
In December 2022, a number of GoDaddy’s customers reported that their websites were being redirected to malicious sites intermittently. GoDaddy subsequently found that an unauthorized third party had gained access to servers hosted in its cPanel environment and had installed malware that caused the redirection of customer websites. The objective of the attacks, according to GoDaddy, was to infect websites and servers with malware for phishing campaigns, malware distribution, and other malicious activities.
In a 10-K filing with the U.S. Securities and Exchange Commission (SEC), GoDaddy has disclosed that the December 2022 incident is linked to two other security events that it experienced in March 2020 and November 2021.
In 2020, the company had detected the compromise of the hosting login credentials of approximately 28,000 hosting customers and a small number of its staff.
In 2021, a rogue actor used a compromised password to gain entry into a provisioning system in the company’s legacy code base for Managed WordPress (MWP), affecting almost 1.2 million active and inactive MWP customers across various GoDaddy brands.
Jeffrey Childers – The AEGIS Alliance – This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.







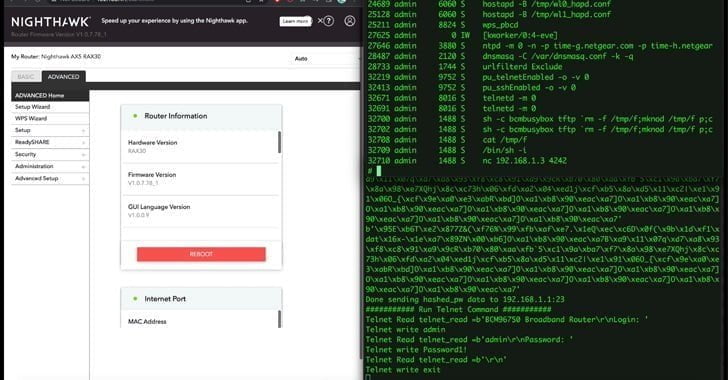


Years? They didn’t know for years? I can’t fathom that. Either they’ve been very lazy and not looking at the code, or they’re part of this.
who the f would trust a godaddy site at all lol
Sharon Bostock tens of thousands have.
John Buettner i dont think ive ever found out what the heck a godaddy is … never used it … the name alone had me on the run…
Sharon Bostock sounds like some repressed father issues.