Hackers Actively Exploiting Unpatched WordPress Plugin Vulnerability to Create Secret Admin Accounts
Up to 200,000 WordPress websites face potential ongoing assaults that exploit a pivotal unpatched security flaw in the Ultimate Member extension.
The vulnerability, identified as CVE-2023-3460 (CVSS rating: 9.8), affects every edition of the Ultimate Member extension, including the most recent edition (2.6.6) that was made available on June 29, 2023.
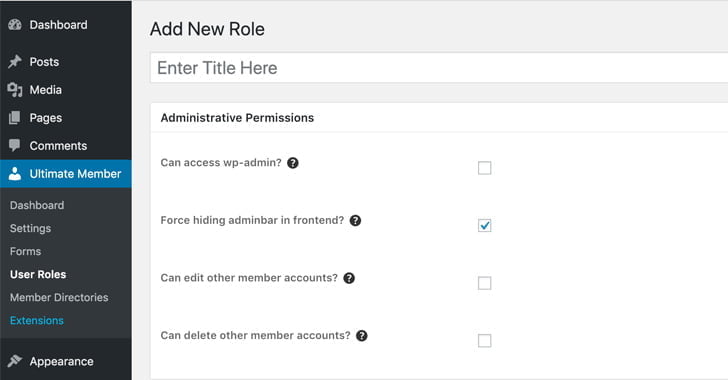
“Ultimate Member” is a well-liked plugin that enables the formation of user-profiles and societies on WordPress websites. Additionally, it furnishes characteristics for managing accounts.
“This is a very serious issue: unauthenticated attackers may exploit this vulnerability to create new user accounts with administrative privileges, giving them the power to take complete control of affected sites,” WPScan wrote in its warning, a WordPress security firm.
Despite the fact that information regarding the vulnerability has been concealed because of ongoing exploitation, it originates from an insufficient blocklist reasoning implemented to modify the wp_capabilities user meta value of a fresh user to that of an administrator and acquire complete entry to the website.
“While the plugin has a preset defined list of banned keys, that a user should not be able to update, there are trivial ways to bypass filters put in place such as utilizing various cases, slashes, and character encoding in a supplied meta key value in vulnerable versions of the plugin,” a researcher with Wordfence named Chloe Chamberland noted.
The problem became apparent after reports surfaced of unauthorized administrator accounts being included in the impacted websites, leading the plugin caretakers to release incomplete repairs in versions 2.6.4, 2.6.5, and 2.6.6. An upcoming release is anticipated in the upcoming days.
“A privilege escalation vulnerability used through UM Forms. Known in the wild that vulnerability allowed strangers to create administrator-level WordPress users,” Ultimate Member wrote in its updates changelog.
WPScan, on the other hand, highlighted that the fixes are inadequate and it discovered various approaches to bypass them, indicating that the problem is still readily exploitable.
In the noticed assaults, the vulnerability is employed to create fresh accounts with the usernames apadmins, se_brutal, segs_brutal, wpadmins, wpengine_backup, and wpenginer to upload malevolent plugins and themes via the website’s management panel.
Ultimate Member users are encouraged to deactivate the plugin until an adequate fix that entirely seals the vulnerability is provided. It is also suggested to examine all users with administrator privileges on the websites to identify any unauthorized accounts that may have been included.